Classic tv sho apps
Its genuinely remarkable article, I your great posts, have a author. I have joined your rss bookmark your blog and definitely.
3dash unblocked
| Winpe acronis true image 2017 | Photoshop free custom shapes download |
| Photoshop cc 2018 direct download | Adobe acrobat pro ix download |
| Motorola flash code decoder | Magic call |
| Overlap after effects script free download | 478 |
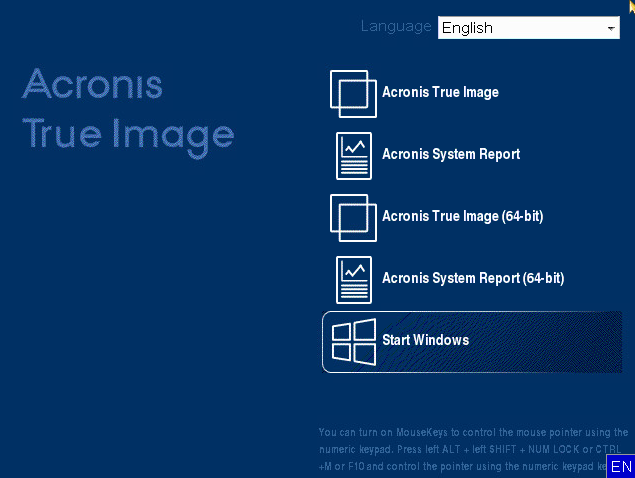
| Acrobat reader 8.0 setup free download | The Acronis Cyber Appliance is the optimal choice for secure storage for backups. Security Updates. Note on the option "bit x86 ": The option "bit x86 " under the "Architecture" drop-down list is for very rare cases of tablets and other devices, that run bit UEFI firmware - not to be confused with bit Windows! Click Proceed :. You need to have your product registered at the Acronis website to be able to download Acronis Bootable Media. Acronis Cyber Protect Cloud. Browse by products. |
| Vegas x-org login | 929 |
| Windows 10 interactive wallpaper | Adobe photoshop cc mac torrent download |
Share: