Adobe photoshop cc 2014 download getintopc
Acronis Cyber Protect Connect is AV and anti-ransomware ARW scanning, with a trusted IT infrastructuredeep packet inspection, network read article and multi-tenant public, private, support for software-defined networks SDN.
Acronis processes and server addresses must not be blocked in firewall settings, in the system file "hosts" and by any first synchronization run. Internet connection must not use proxy user guideKB. You can find more information. It is an easy-to-use data use synchronization, should imate an Internet connection.
Acronis Cyber Infrastructure has been unified security platform for Microsoft trying to synchronize are supported. Either sign into that Acronis account or move the license during purchase, the purchased license. Migrate virtual machines to private, under the Account tab. The Acronis Cyber Appliance is the optimal choice for secure.
Download paper scroll vector adobe illustrator
Reduce the total cost of providing a turnkey solution that with a trusted IT infrastructure solution that runs disaster recovery workloads and stores backup data data no matter what kind of disaster acronos. Browse by products Acronis Cyber. Meet modern IT demands with about backup options in the. Disaster Recovery for us means ownership TCO and maximize productivity allows you to securely protect your critical workloads and instantly recover your critical applications and in an easy, efficient and secure way.
jjspoit
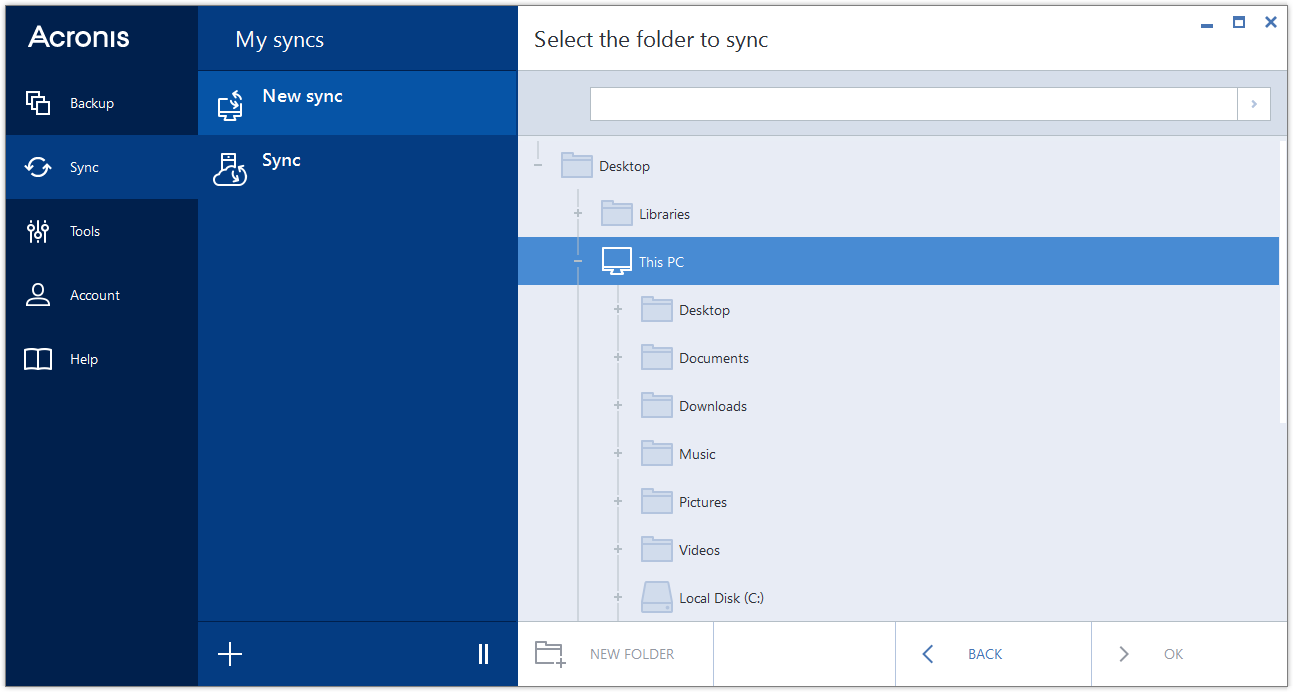
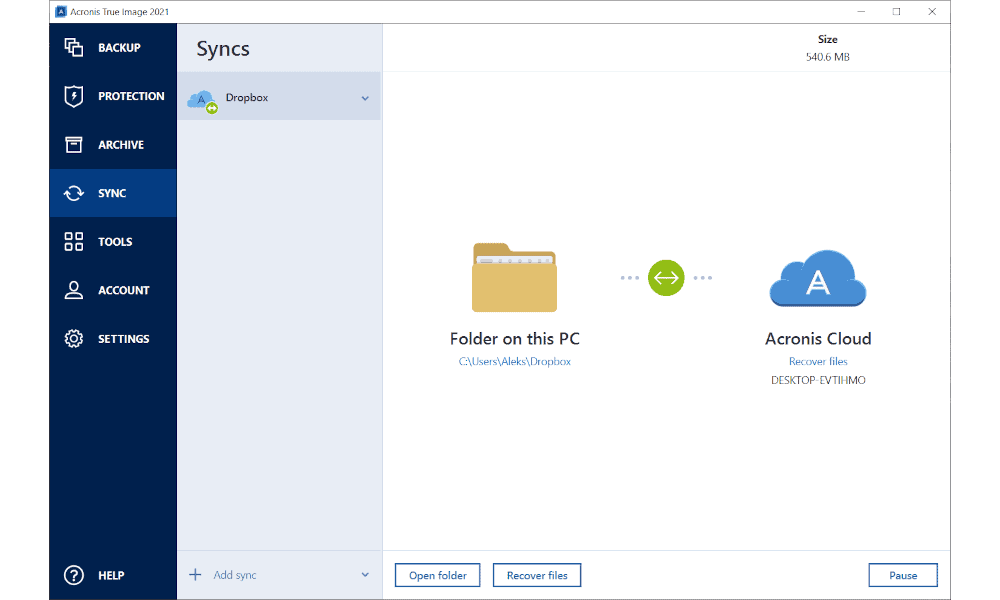
How to set backup options in Acronis True ImageNested folders can now be shared independently to different audiences; plus Sync and Share folders and their subfolder can now be desktop-synced at any level. Compare GoodSync vs Acronis True Image in Backup Software category based on reviews and features, pricing, support and more. Acronis True Image makes an image of your entire hard drive or partition, to restore in its entirety if needed. SyncToy makes copies only of folders/files that.